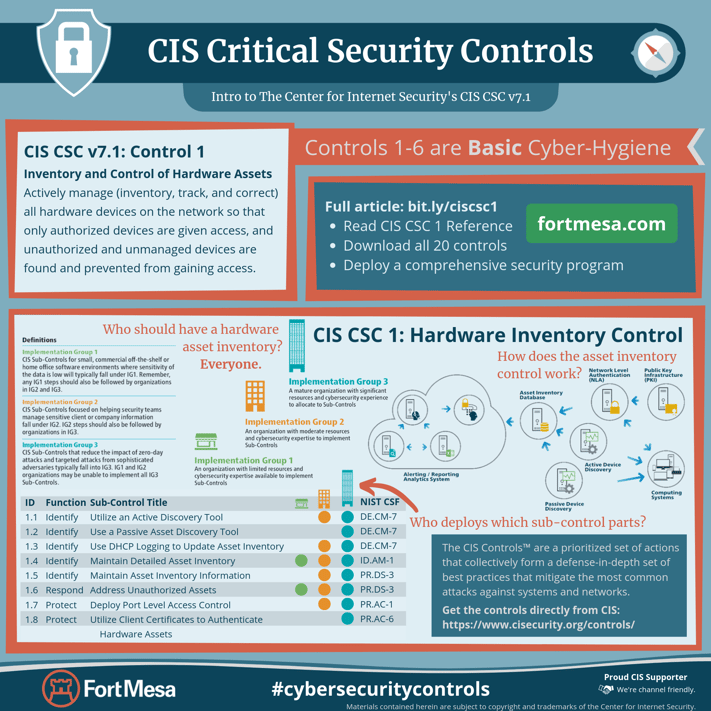
CSC 1: Inventory and Control of Hardware Assets
Actively manage (inventory, track, and correct) all hardware devices on the network so that only authorized devices are given access, and unauthorized and unmanaged devices are found and prevented from gaining access.
Why is this control critical?
Attackers, who can be located anywhere in the world, are continuously scanning the address space of target organizations, waiting for new and possibly unprotected systems to be attached to the network. They are particularly interested in devices which come and go off of the enterprise’s network such as laptops or Bring-Your-Own-Device (BYOD) which might be out of synchronization with security updates or might already be compromised. Attacks can take advantage of new hardware that is installed on the network one evening but not configured and patched with appropriate security updates until the following day. Even devices that are not visible from the Internet can be used by attackers who have already gained internal access and are hunting for internal pivot points or victims. Additional systems that connect to the enterprise’s network (e.g., demonstration systems, temporary test systems, guest networks) should also be managed carefully and/or isolated in order to prevent adversarial access from affecting the security of enterprise operations.
Large, complex enterprises understandably struggle with the challenge of managing intricate, fast-changing environments. But attackers have shown the ability, patience, and willingness to “inventory and control” our assets at very large scale in order to support their opportunities.
Managed control of all devices also plays a critical role in planning and executing system backup, incident response, and recovery.
Who should deploy this control?
Answer: Everyone
The Center for Internet Security has broken down all of the Critical Security Controls in a way that allows organizations of all types to implement the security defenses that are right for them.
Before we dig into the details of CIS CSC 1 let's quickly explore the CSC Implementation Groups.
Implementation Groups
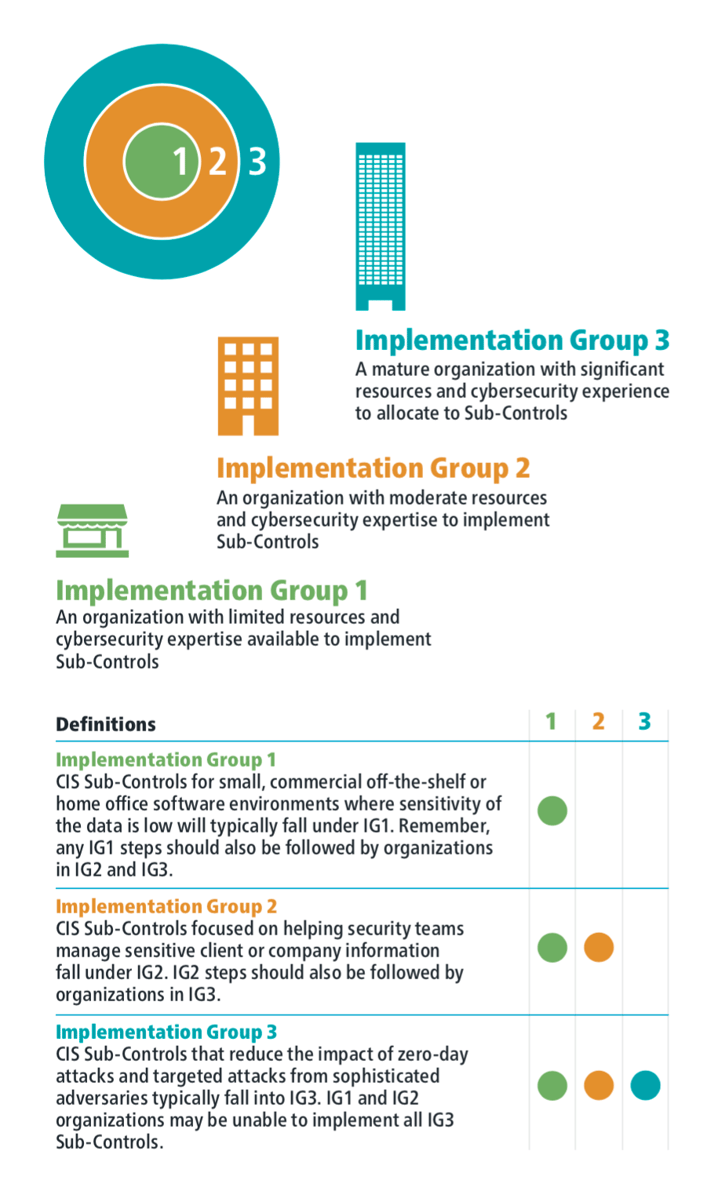
Control Details
| Sub-Control | Security Function |
IG1 |
IG2 |
IG3 |
NIST CSF |
| 1.1 | Identify | ⬤ | ⬤ | DE.CM-7 | |
|
Utilize an Active Discovery Tool Utilize an active discovery tool to identify devices connected to the organization's network and update the hardware asset inventory. |
|||||
| 1.2 | Identify | ⬤ | DE.CM-7 | ||
|
Use a Passive Asset Discovery Tool Utilize a passive discovery tool to identify devices connected to the organization's network and automatically update the organization's hardware asset inventory. |
|||||
| 1.3 | Identify | ⬤ | ⬤ | DE.CM-7 | |
|
Use DHCP Logging to Update Asset Inventory Use Dynamic Host Configuration Protocol (DHCP) logging on all DHCP servers or IP address management tools to update the organization's hardware asset inventory. |
|||||
| 1.4 | Identify | ⬤ | ⬤ | ⬤ | ID.AM-1, PR.DS-3 |
|
Maintain Detailed Asset Inventory Maintain an accurate and up-to-date inventory of all technology assets with the potential to store or process information. This inventory shall include all hardware assets, whether connected to the organization's network or not. |
|||||
| 1.5 | Identify | ⬤ | ⬤ | PR.DS-3 | |
|
Maintain Asset Inventory Information Ensure that the hardware asset inventory records the network address, hardware address, machine name, data asset owner, and department for each asset and whether the hardware asset has been approved to connect to the network. |
|||||
| 1.6 | Respond | ⬤ | ⬤ | ⬤ | PR.DS-3 |
|
Address Unauthorized Assets Ensure that unauthorized assets are either removed from the network, quarantined or the inventory is updated in a timely manner. |
|||||
| 1.7 | Protect | ⬤ | ⬤ | PR.AC-1 | |
|
Deploy Port Level Access Control Utilize port level access control, following 802.1x standards, to control which devices can authenticate to the network. The authentication system shall be tied into the hardware asset inventory data to ensure only authorized devices can connect to the network. |
|||||
| 1.8 | Protect | ⬤ | PR.AC-6 | ||
|
Utilize Client Certificates to Authenticate Hardware Assets Use client certificates to authenticate hardware assets connecting to the organization's trusted network. |
|||||
Procedures and Tools
This Control requires both technical and procedural actions, united in a process that accounts for and manages the inventory of hardware and all associated information throughout its life cycle. It links to business governance by establishing information/asset owners who are responsible for each component of a business process that includes information, software, and hardware. Organizations can use large-scale, comprehensive enterprise products to maintain IT asset inventories. Others use more modest tools to gather the data by sweeping the network, and manage the results separately in a database.
Maintaining a current and accurate view of IT assets is an ongoing and dynamic process. Organizations can actively scan on a regular basis, sending a variety of different packet types to identify devices connected to the network. Before such scanning can take place, organizations should verify that they have adequate bandwidth for such periodic scans by consulting load history and capacities for their networks.
In conducting inventory scans, scanning tools could send traditional ping packets (ICMP Echo Request) looking for ping responses to identify a system at a given IP address. Because some systems block inbound ping packets, in addition to traditional pings, scanners can also identify devices on the network using transmission control protocol (TCP), synchronize (SYN), or acknowledge (ACK) packets. Once they have identified IP addresses of devices on the network, some scanners provide robust fingerprinting features to determine the operating system type of the discovered machine.
In addition to active scanning tools that sweep the network, other asset identification tools passively listen on network interfaces for devices to announce their presence by sending traffic. Such passive tools can be connected to switch span ports at critical places in the network to view all data flowing through such switches, maximizing the chance of identifying systems communicating through those switches.
Many organizations also pull information from network assets such as switches and routers regarding the machines connected to the network. Using securely authenticated and encrypted network management protocols, tools can retrieve media access control (MAC) addresses and other information from network devices that can be reconciled with the organization’s asset inventory of servers, workstations, laptops, and other devices. Once MAC addresses are confirmed, switches should implement 802.1x and Network Access Control (NAC) to only allow authorized systems that are properly configured to connect to the network.
Wireless devices (and wired laptops) may periodically join a network and then disappear, making the inventory of currently available systems very dynamic. Likewise, virtual machines can be difficult to track in asset inventories when they are shut down or paused. Additionally, remote machines accessing the network using virtual private network (VPN) technology may appear on the network for a time, and then be disconnected from it. Whether physical or virtual, each machine using an IP address should be included in an organization’s asset inventory.
System Entity Relationship Diagram
-2.jpeg?width=933&name=download%20(1)-2.jpeg)
About the CIS Controls
The CIS Controls™ are a prioritized set of actions that collectively form a defense-in-depth set of best practices that mitigate the most common attacks against systems and networks.
CIS holds trademarks and copyright on all control materials however the controls are free to use in your organization and can be downloaded directly from CIS at:
https://www.cisecurity.org/controls/
Last updated 2019-09-20.
FortMesa Makes Asset Inventory Easy
We combine your human intelligence with our automation to:
-
Guide your stakeholders in developing their own security plan.
-
Continuously evolve strategy and stay in compliance.
-
Comprehensive cyber risk management and security options -- in an app.

.png?width=50&name=output-onlinepngtools%20(1).png)
.png?width=50&name=output-onlinepngtools%20(3).png)
.png?width=50&name=output-onlinepngtools%20(2).png)


 Team Security Culture is an App Away
Team Security Culture is an App Away

