CSC 2: Inventory and Control of Software Assets
Actively manage (inventory, track, and correct) all software on the network so that only authorized software is installed and can execute, and that all unauthorized and unmanaged software is found and prevented from installation or execution.
Why is this control critical?
Attackers continuously scan target organizations looking for vulnerable versions of software that can be remotely exploited. Some attackers also distribute hostile web pages, document files, media files, and other content via their own web pages or otherwise trustworthy third-party sites. When unsuspecting victims access this content with a vulnerable browser or other client-side program, attackers compromise their machines, often installing backdoor programs and bots that give the attacker long-term control of the system. Some sophisticated attackers may use zero-day exploits, which take advantage of previously unknown vulnerabilities for which no patch has yet been released by the software vendor. Without proper knowledge or control of the software deployed in an organization, defenders cannot properly secure their assets.
Poorly controlled machines are more likely to be either running software that is unneeded for business purposes (introducing potential security flaws), or running malware introduced by an attacker after a system is compromised. Once a single machine has been exploited, attackers often use it as a staging point for collecting sensitive information from the compromised system and from other systems connected to it. In addition, compromised machines are used as a launching point for movement throughout the network and partnering networks. In this way, attackers may quickly turn one compromised machine into many. Organizations that do not have complete software inventories are unable to find systems running vulnerable or malicious software to mitigate problems or root out attackers.
Managed control of all software also plays a critical role in planning and executing system backup, incident response, and recovery.
Who should deploy this control?
Answer: Everyone
The Center for Internet Security has broken down all of the Critical Security Controls in a way that allows organizations of all types to implement the security defenses that are right for them.
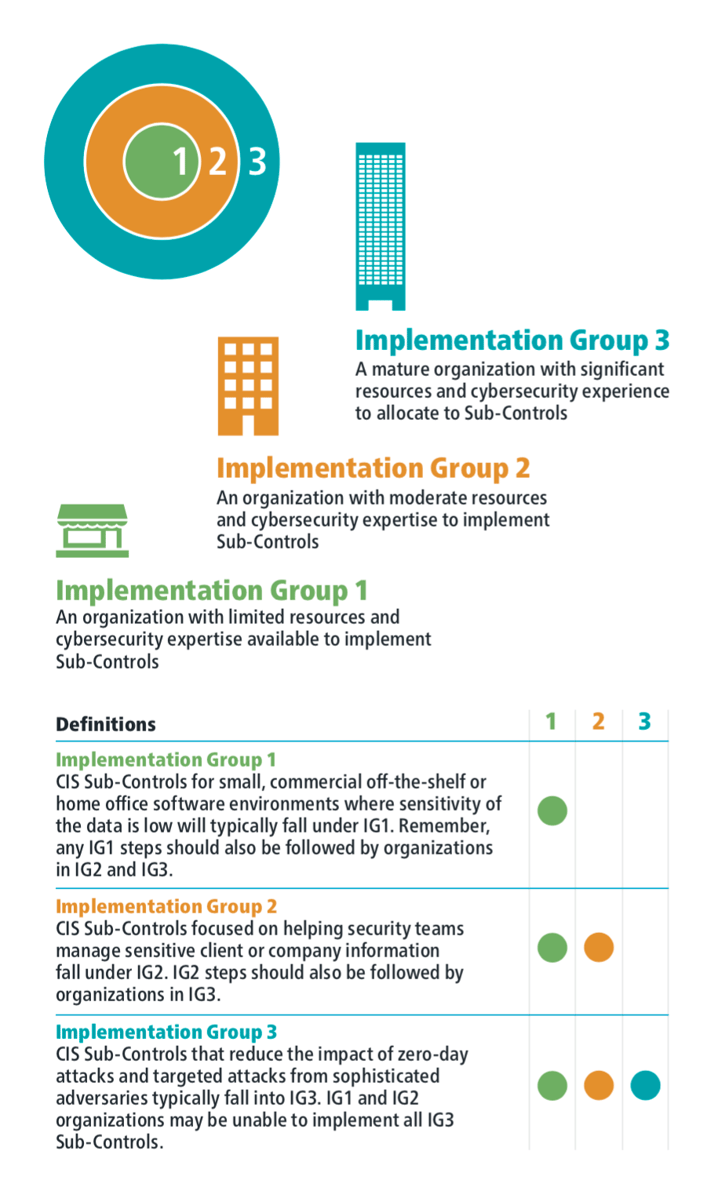
Before we dig into the details of CIS CSC 2 let's quickly explore the CSC Implementation Groups.
Implementation Groups
Control Details
| Sub-Control | Security Function |
IG1 |
IG2 |
IG3 |
NIST CSF |
| 2.1 | Identify | ⬤ | ⬤ | ⬤ | ID.AM-2 |
|
Maintain Inventory of Authorized Software Maintain an up-to-date list of all authorized software that is required in the enterprise for any business purpose on any business system. |
|||||
| 2.2 | Identify | ⬤ | ⬤ | ⬤ | ID.AM-2 |
|
Ensure Software is Supported by Vendor Ensure that only software applications or operating systems currently supported and receiving vendor updates are added to the organization's authorized software inventory. Unsupported software should be tagged as unsupported in the inventory system. |
|||||
| 2.3 | Identify | ⬤ | ⬤ | DE.CM-7 | |
|
Utilize Software Inventory Tools Utilize software inventory tools throughout the organization to automate the documentation of all software on business systems. |
|||||
| 2.4 | Identify | ⬤ | ⬤ | ID.AM-2 | |
|
Track Software Inventory Information The software inventory system should track the name, version, publisher, and install date for all software, including operating systems authorized by the organization. |
|||||
| 2.5 | Identify | ⬤ | ⬤ | ID.AM-1, ID.AM-2 | |
|
Integrate Software and Hardware Asset Inventories The software inventory system should be tied into the hardware asset inventory so all devices and associated software are tracked from a single location. |
|||||
| 2.6 | Respond | ⬤ | ⬤ | ⬤ | DE.CM-7 |
|
Address unapproved software Ensure that unauthorized software is either removed or the inventory is updated in a timely manner |
|||||
| 2.7 | Protect | ⬤ | PR.DS-6, DE.CM-7 | ||
|
Utilize Application Whitelisting Utilize application whitelisting technology on all assets to ensure that only authorized software executes and all unauthorized software is blocked from executing on assets. |
|||||
| 2.8 | Protect | ⬤ | PR.DS-6, DE.CM-7 | ||
|
Implement Application Whitelisting of Libraries The organization's application whitelisting software must ensure that only authorized software libraries (such as *.dll, *.ocx, *.so, etc.) are allowed to load into a system process. |
|||||
| 2.9 | Protect | ⬤ | PR.DS-6, DE.CM-7 | ||
|
Implement Application Whitelisting of Scripts The organization's application whitelisting software must ensure that only authorized, digitally signed scripts (such as *.ps1, *.py, macros, etc.) are allowed to run on a system. |
|||||
| 2.10 | Protect | ⬤ | - | ||
|
Physically or Logically Segregate High Risk Applications Physically or logically segregated systems should be used to isolate and run software that is required for business operations but incurs higher risk for the organization. |
|||||
Procedures and Tools
Whitelisting can be implemented using a combination of commercial whitelisting tools, policies, or application execution tools that come with anti-virus suites and popular operating systems. Commercial software and asset inventory tools are widely available and in use in many enterprises today. The best of these tools provide an inventory check of hundreds of common applications used in enterprises, pulling information about the patch level of each installed program to ensure that it is the latest version and leveraging standardized application names, such as those found in the common platform enumeration (CPE) specification.
Features that implement whitelists are included in many modern endpoint security suites and even natively implemented in certain versions of major operating systems. Moreover, commercial solutions are increasingly bundling together anti-virus, anti-spyware, personal firewall, and host-based intrusion detection systems (IDS) and intrusion prevention systems (IPS), along with application white and black listing. In particular, most endpoint security solutions can look at the name, file system location, and/or cryptographic hash of a given executable to determine whether the application should be allowed to run on the protected machine. The most effective of these tools offer custom whitelists based on executable path, hash, or regular expression matching. Some even include a gray list function that allows administrators to define rules for execution of specific programs only by certain users and at certain times of day.
System Entity Relationship Diagram
.jpeg?width=1077&name=download%20(2).jpeg)
About the CIS Controls
The CIS Controls™ are a prioritized set of actions that collectively form a defense-in-depth set of best practices that mitigate the most common attacks against systems and networks.
CIS holds trademarks and copyright on all control materials however the controls are free to use in your organization and can be downloaded directly from CIS at:
https://www.cisecurity.org/controls/
Last updated 2019-09-30.

.png?width=50&name=output-onlinepngtools%20(1).png)
.png?width=50&name=output-onlinepngtools%20(3).png)
.png?width=50&name=output-onlinepngtools%20(2).png)
.png?width=816&name=How%20it%20Works%20part%20deux%20(2).png)



 Team Security Culture is an App Away
Team Security Culture is an App Away.png?width=150&name=Copy%20of%20CIS%20CSC%20v7.1%20Control%202%20Poster%20(1).png)