CSC 3: Continuous Vulnerability Management
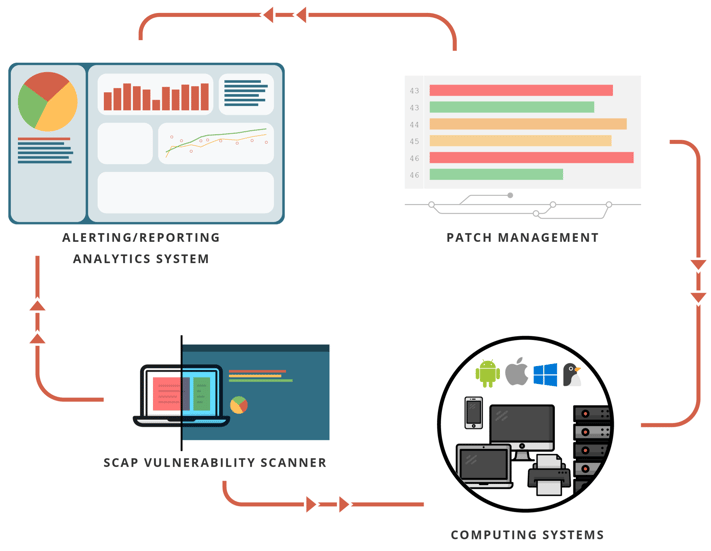
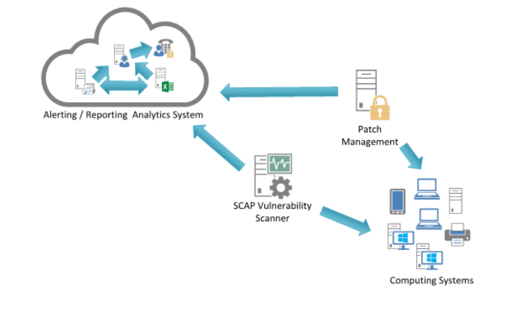
Continuously acquire, assess, and take action on new information in order to identify vulnerabilities, remediate, and minimize the window of opportunity for attackers.
Why is this control critical?
Cyber defenders must operate in a constant stream of new information: software updates, patches, security advisories, threat bulletins, etc. Understanding and managing vulnerabilities has become a continuous activity, requiring significant time, attention, and resources.
Attackers have access to the same information and can take advantage of gaps between the appearance of new knowledge and remediation. For example, when researchers report new vulnerabilities, a race starts among all parties, including: attackers (to “weaponize,” deploy an attack, exploit), vendors (to develop, deploy patches or signatures and updates), and defenders (to assess risk, regression-test patches, install).
Organizations that do not scan for vulnerabilities and proactively address discovered flaws face a significant likelihood of having their computer systems compromised. Defenders face particular challenges in scaling remediation across an entire enterprise, and prioritizing actions with conflicting priorities, and sometimes uncertain side effects.
Who should deploy this control?
Answer: Everyone
The Center for Internet Security has broken down all of the Critical Security Controls in a way that allows organizations of all types to implement the security defenses that are right for them.
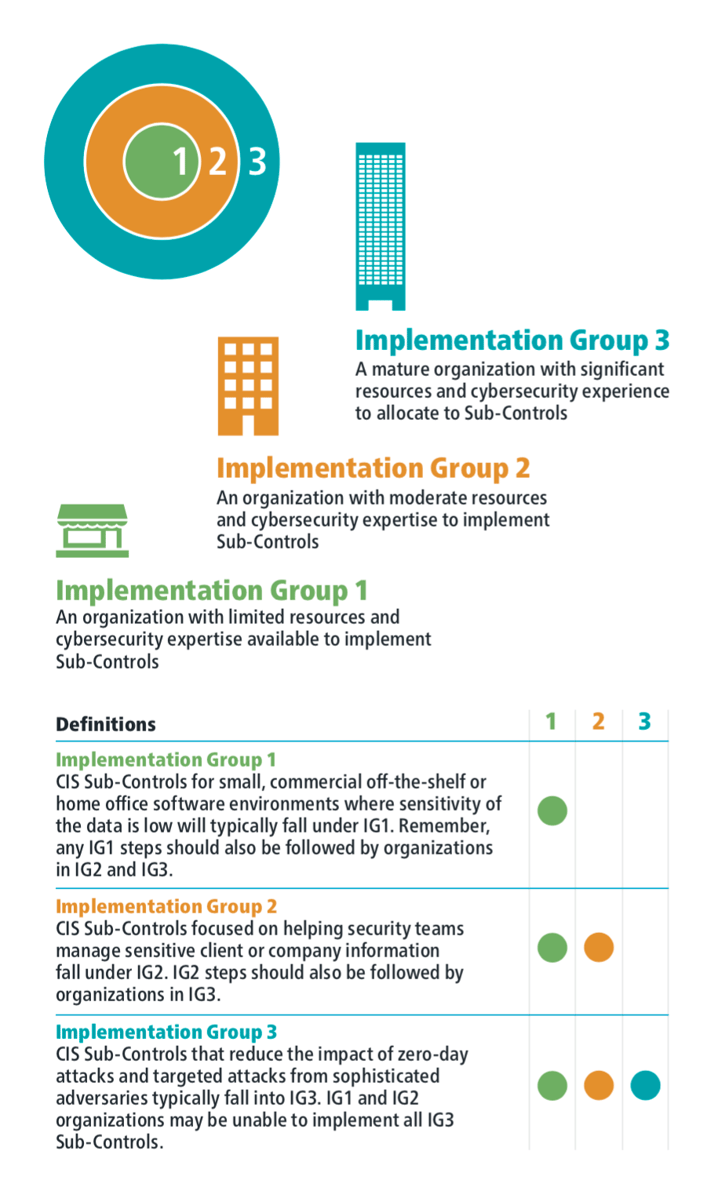
Before we dig into the details of CIS CSC 3 let's quickly explore the CSC Implementation Groups.
Implementation Groups
Control Details
| Sub-Control | Security Function |
IG1 |
IG2 |
IG3 |
NIST CSF |
| 3.1 | Detect | ⬤ | ⬤ | ID.RA-1,DE.CM-8 | |
|
Run Automated Vulnerability Scanning Tools Utilize an up-to-date Security Content Automation Protocol (SCAP) compliant vulnerability scanning tool to automatically scan all systems on the network on a weekly or more frequent basis to identify all potential vulnerabilities on the organization's systems. |
|||||
| 3.2 | Detect | ⬤ | ⬤ | DE.CM-8 | |
|
Perform Authenticated Vulnerability Scanning Perform authenticated vulnerability scanning with agents running locally on each system or with remote scanners that are configured with elevated rights on the system being tested. |
|||||
| 3.3 | Protect | ⬤ | ⬤ | ||
|
Protect Dedicated Assessment Accounts Use a dedicated account for authenticated vulnerability scans, which should not be used for any other administrative activities and should be tied to specific machines at specific IP addresses. |
|||||
| 3.4 | Protect | ⬤ | ⬤ | ⬤ | |
|
Deploy Automated Operating System Patch Management Tools Deploy automated software update tools in order to ensure that the operating systems are running the most recent security updates provided by the software vendor. |
|||||
| 3.5 | Protect | ⬤ | ⬤ | ⬤ | |
|
Deploy Automated Software Patch Management Tools Deploy automated software update tools in order to ensure that third-party software on all systems is running the most recent security updates provided by the software vendor. |
|||||
| 3.6 | Respond | ⬤ | ⬤ | ||
|
Compare Back-to-Back Vulnerability Scans Regularly compare the results from consecutive vulnerability scans to verify that vulnerabilities have been remediated in a timely manner. |
|||||
| 3.7 | Respond | ⬤ | ⬤ |
RS.MI-3, ID.RA-5, PR.IP-12 |
|
|
Utilize a Risk-Rating Process Utilize a risk-rating process to prioritize the remediation of discovered vulnerabilities. |
|||||
Procedures and Tools
A large number of vulnerability scanning tools are available to evaluate the security configuration of systems. Some enterprises have also found commercial services using remotely managed scanning appliances to be effective. To help standardize the definitions of discovered vulnerabilities in multiple departments of an organization or even across organizations, it is preferable to use vulnerability scanning tools that measure security flaws and map them to vulnerabilities and issues categorized using one or more of the following industry-recognized vulnerability, configuration, and platform classification schemes and languages: CVE, CCE, OVAL, CPE, CVSS, and/or XCCDF.
Advanced vulnerability scanning tools can be configured with user credentials to login to scanned systems and perform more comprehensive scans than what can be achieved without login credentials. The frequency of scanning activities, however, should increase as the diversity of an organization’s systems increases to account for the varying patch cycles of each vendor.
In addition to the scanning tools that check for vulnerabilities and misconfigurations across the network, various free and commercial tools can evaluate security settings and configurations of local machines on which they are installed. Such tools can provide fine-grained insight into unauthorized changes in configuration or the inadvertent introduction of security weaknesses by administrators.
Effective organizations link their vulnerability scanners with problem-ticketing systems that automatically monitor and report progress on fixing problems, and that makes unmitigated critical vulnerabilities visible to higher levels of management to ensure the problems are solved.
The most effective vulnerability scanning tools compare the results of the current scan with previous scans to determine how the vulnerabilities in the environment have changed over time. Security personnel use these features to conduct vulnerability trending from month to month.
As vulnerabilities related to unpatched systems are discovered by scanning tools, security personnel should determine and document the amount of time that elapses between the public release of a patch for the system and the occurrence of the vulnerability scan. If this time window exceeds the organization’s benchmarks for deployment of the given patch’s criticality level, security personnel should note the delay and determine if a deviation was formally documented for the system and its patch. If not, the security team should work with management to improve the patching process.
Additionally, some automated patching tools may not detect or install certain patches due to an error by the vendor or administrator. Because of this, all patch checks should reconcile system patches with a list of patches each vendor has announced on its website.
System Entity Relationship Diagram
About the CIS Controls
The CIS Controls™ are a prioritized set of actions that collectively form a defense-in-depth set of best practices that mitigate the most common attacks against systems and networks.
CIS holds trademarks and copyright on all control materials however the controls are free to use in your organization and can be downloaded directly from CIS at:
https://www.cisecurity.org/controls/
Last updated 2020-01-11.

.png?width=50&name=output-onlinepngtools%20(1).png)
.png?width=50&name=output-onlinepngtools%20(3).png)
.png?width=50&name=output-onlinepngtools%20(2).png)

 Kickstart Your Security Agenda
Kickstart Your Security Agenda




