CSC 4: Controlled Use of Administrative Privileges
The processes and tools used to track/control/prevent/correct the use, assignment, and configuration of administrative privileges on computers, networks, and applications.
Why is this control critical?
The misuse of administrative privileges is a primary method for attackers to spread inside a target enterprise. Two very common attacker techniques take advantage of uncontrolled administrative privileges. In the first, a workstation user running as a privileged user is fooled into opening a malicious email attachment, downloading and opening a file from a malicious website, or simply surfing to a website hosting attacker content that can automatically exploit browsers. The file or exploit contains executable code that runs on the victim’s machine either automatically or by tricking the user into executing the attacker’s content. If the victim user’s account has administrative privileges, the attacker can take over the victim’s machine completely and install keystroke loggers, sniffers, and remote control software to find administrative passwords and other sensitive data. Similar attacks occur with email. An administrator inadvertently opens an email that contains an infected attachment and this is used to obtain a pivot point within the network that is used to attack other systems.
The second common technique used by attackers is elevation of privileges by guessing or cracking a password for an administrative user to gain access to a target machine. If administrative privileges are loosely and widely distributed, or identical to passwords used on less critical systems, the attacker has a much easier time gaining full control of systems, because there are many more accounts that can act as avenues for the attacker to compromise administrative privileges.
Who should deploy this control?
Answer: Everyone
The Center for Internet Security has broken down all of the Critical Security Controls in a way that allows organizations of all types to implement the security defenses that are right for them.
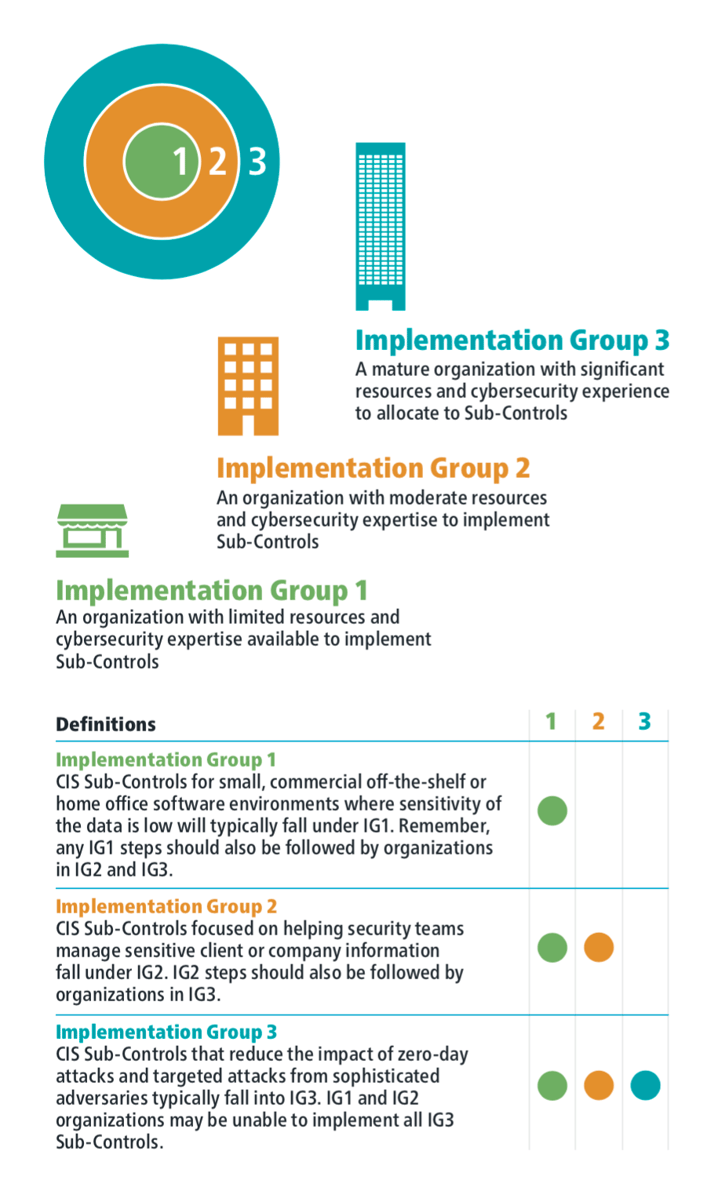
Before we dig into the details of CIS CSC 4 let's quickly explore the CSC Implementation Groups.
Implementation Groups
Control Details
| Sub-Control | Security Function |
IG1 |
IG2 |
IG3 |
NIST CSF |
| 4.1 | Detect | ⬤ | ⬤ | PR.AC-1 | |
|
Maintain Inventory of Administrative Accounts Use automated tools to inventory all administrative accounts, including domain and local accounts, to ensure that only authorized individuals have elevated privileges. |
|||||
| 4.2 | Protect | ⬤ | ⬤ | ⬤ | PR.AC-1 |
|
Change Default Passwords Before deploying any new asset, change all default passwords to have values consistent with administrative level accounts. |
|||||
| 4.3 | Protect | ⬤ | ⬤ | ⬤ | PR.AC-4 |
|
Ensure the Use of Dedicated Administrative Accounts Ensure that all users with administrative account access use a dedicated or secondary account for elevated activities. This account should only be used for administrative activities and not Internet browsing, email, or similar activities. |
|||||
| 4.4 | Protect | ⬤ | ⬤ | ||
|
Use Unique Passwords Where multi-factor authentication is not supported (such as local administrator, root, or service accounts), accounts will use passwords that are unique to that system. |
|||||
| 4.5 | Protect | ⬤ | ⬤ | PR.AC-7 | |
|
Use Multi-Factor Authentication for All Administrative Access Use multi-factor authentication and encrypted channels for all administrative account access. |
|||||
| 4.6 | Protect | ⬤ | |||
|
Use Dedicated Workstations For All Administrative Tasks Ensure administrators use a dedicated machine for all administrative tasks or tasks requiring administrative access. This machine will be segmented from the organization's primary network and not be allowed Internet access. This machine will not be used for reading email, composing documents, or browsing the Internet. |
|||||
| 4.7 | Protect | ⬤ | ⬤ | PR.PT-3 | |
|
Limit Access to Scripting Tools Limit access to scripting tools (such as Microsoft® PowerShell and Python) to only administrative or development users with the need to access those capabilities. |
|||||
| 4.8 | Detect | ⬤ | ⬤ | DE.CM-7 | |
|
Log and Alert on Changes to Administrative Group Membership Configure systems to issue a log entry and alert when an account is added to or removed from any group assigned administrative privileges. |
|||||
| 4.9 | Detect | ⬤ | ⬤ | DE.CM-7 | |
|
Log and Alert on Unsuccessful Administrative Account Login Configure systems to issue a log entry and alert on unsuccessful logins to an administrative account. |
|||||
Procedures and Tools
Built-in operating system features can extract lists of accounts with super-user privileges, both locally on individual systems and on overall domain controllers. To verify that users with high-privileged accounts do not use such accounts for day-to-day web surfing and email reading, security personnel should periodically gather a list of running processes to determine whether any browsers or email readers are running with high privileges. Such information gathering can be scripted, with short shell scripts searching for a dozen or more different browsers, email readers, and document editing programs running with high privileges on machines. Some legitimate system administration activity may require the execution of such programs over the short term, but long-term or frequent use of such programs with administrative privileges could indicate that an administrator is not adhering to this Control.
An excellent resource is:
The NIST Digital Identity Guidelines (https://pages.nist.gov/800-63-3/)
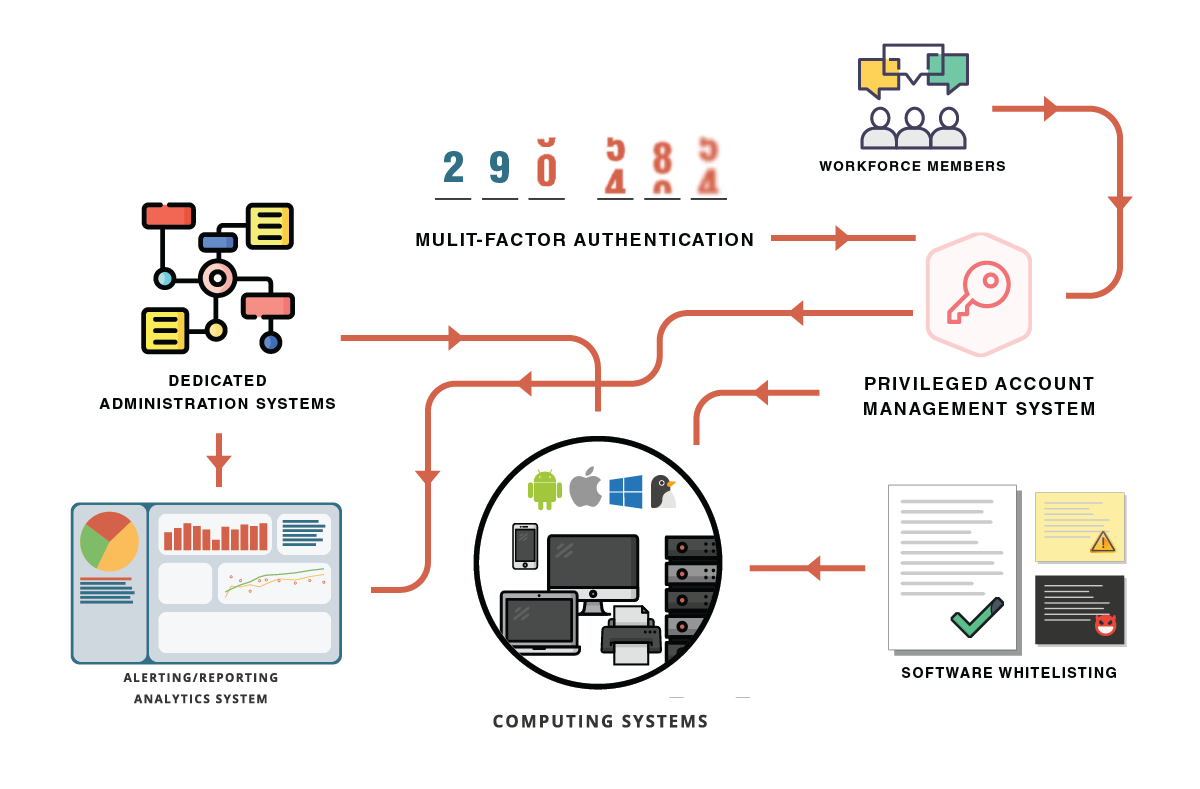
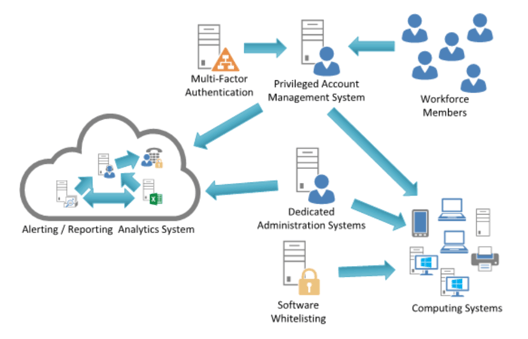
System Entity Relationship Diagram
About the CIS Controls
The CIS Controls™ are a prioritized set of actions that collectively form a defense-in-depth set of best practices that mitigate the most common attacks against systems and networks.
CIS holds trademarks and copyright on all control materials however the controls are free to use in your organization and can be downloaded directly from CIS at:
https://www.cisecurity.org/controls/
Last updated 2020-1-31.

.png?width=50&name=output-onlinepngtools%20(1).png)
.png?width=50&name=output-onlinepngtools%20(3).png)
.png?width=50&name=output-onlinepngtools%20(2).png)
.png?width=466&name=FortMesa%20Diagram%20(3).png)


 Kickstart Your Security Agenda
Kickstart Your Security Agenda


