CSC 5: Secure Configurations for Hardware and Software on Mobile Devices, Laptops, Workstations, and Servers
Establish, implement, and actively manage (track, report on, correct) the security configuration of mobile devices, laptops, servers, and workstations using a rigorous configuration management and change control process in order to prevent attackers from exploiting vulnerable services and settings.
Why is this control critical?
As delivered by manufacturers and resellers, the default configurations for operating systems and applications are normally geared towards ease-of-deployment and ease-of-use – not security. Basic controls, open services and ports, default accounts or passwords, older (vulnerable) protocols, and pre-installation of unneeded software can be exploitable in their default state. Developing configuration settings with good security properties is a complex task beyond the ability of individual users, requiring analysis of potentially hundreds or thousands of options in order to make good choices (the Procedures and Tools section below provides resources for secure configurations). Even if a strong initial configuration is developed and installed, it must be continually managed to avoid security “decay” as software is updated or patched, new security vulnerabilities are reported, and configurations are “tweaked” to allow the installation of new software or support new operational requirements. If not, attackers will find opportunities to exploit both network accessible services and client software.Who should deploy this control?
Answer: Everyone
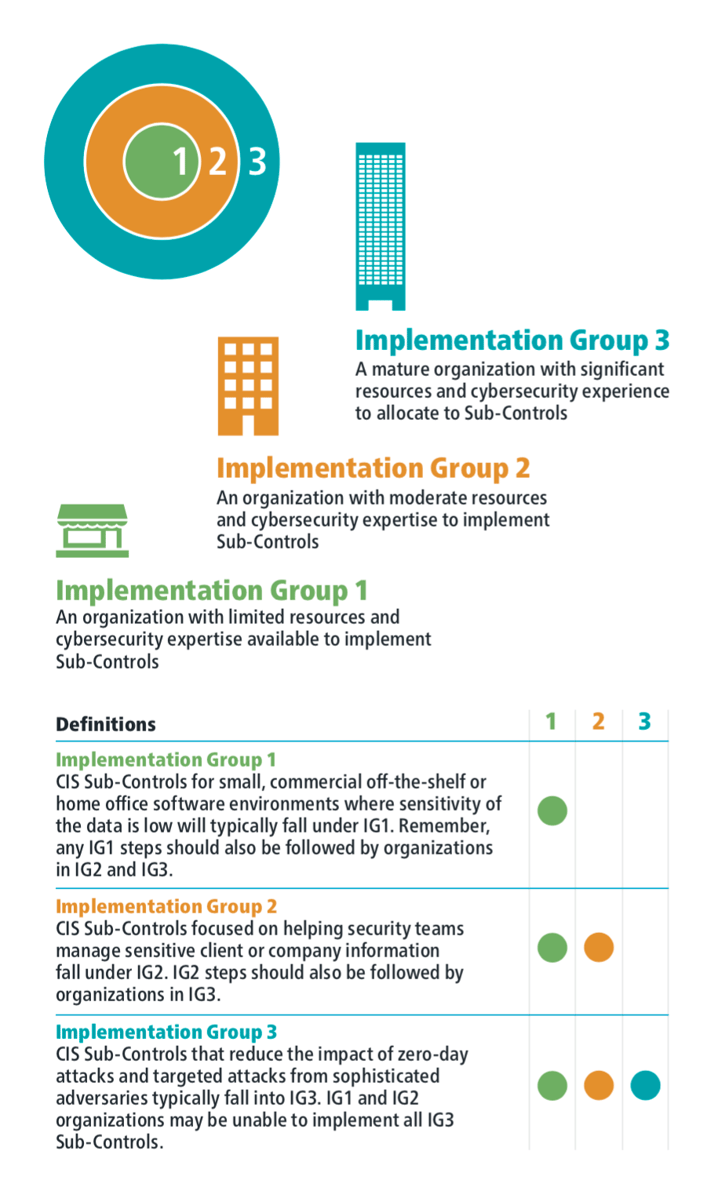
The Center for Internet Security has broken down all of the Critical Security Controls in a way that allows organizations of all types to implement the security defenses that are right for them.
Before we dig into the details of CIS CSC 4 let's quickly explore the CSC Implementation Groups.
Implementation Groups
Control Details
| Sub-Control | Security Function |
IG1 |
IG2 |
IG3 |
NIST CSF |
| 5.1 | Protect | ⬤ | ⬤ | ⬤ | PR.IP-1 |
|
Establish Secure Configurations Maintain documented, standard security configuration standards for all authorized operating systems and software. |
|||||
| 5.2 | Protect | ⬤ | ⬤ | PR.IP-1 | |
|
Maintain Secure Images Maintain secure images or templates for all systems in the enterprise based on the organization's approved configuration standards. Any new system deployment or existing system that becomes compromised should be imaged using one of those images or templates. |
|||||
| 5.3 | Protect | ⬤ | ⬤ | PR.IP-1 | |
|
Securely Store Master Images Store the master images and templates on securely configured servers, validated with integrity monitoring tools, to ensure that only authorized changes to the images are possible. |
|||||
| 5.4 | Protect | ⬤ | ⬤ | ||
|
Deploy System Configuration Management Tools Deploy system configuration management tools that will automatically enforce and redeploy configuration settings to systems at regularly scheduled intervals. |
|||||
| 5.5 | Detect | ⬤ | ⬤ | DE.CM-8 | |
|
Implement Automated Configuration Monitoring Systems Utilize a Security Content Automation Protocol (SCAP) compliant configuration monitoring system to verify all security configuration elements, catalog approved exceptions, and alert when unauthorized changes occur. |
|||||
Procedures and Tools
Rather than start from scratch developing a security baseline for each software system, organizations should start from publicly developed, vetted, and supported security benchmarks, security guides, or checklists. Excellent resources include:- The CIS Benchmarks™ Program (https://www.cisecurity.org/cis-benchmarks/)
- The NIST National Checklist Program (https://nvd.nist.gov/ncp/repository)
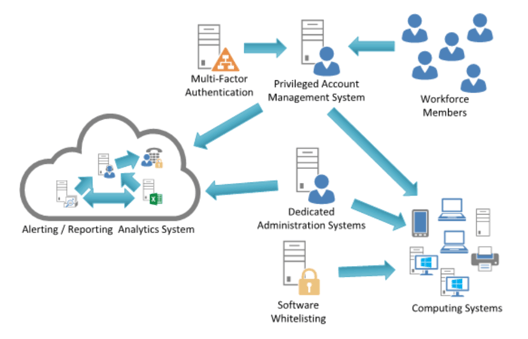
System Entity Relationship Diagram
About the CIS Controls
The CIS Controls™ are a prioritized set of actions that collectively form a defense-in-depth set of best practices that mitigate the most common attacks against systems and networks.
CIS holds trademarks and copyright on all control materials however the controls are free to use in your organization and can be downloaded directly from CIS at:
https://www.cisecurity.org/controls/
Last updated 2020-1-31.

.png?width=50&name=output-onlinepngtools%20(1).png)
.png?width=50&name=output-onlinepngtools%20(3).png)
.png?width=50&name=output-onlinepngtools%20(2).png)
.png?width=466&name=FortMesa%20Diagram%20(3).png)


 Kickstart Your Security Agenda
Kickstart Your Security Agenda


