MSP Cyber Sales Playbook
Use customer trust to sell more cyber with the CANT Cyber Sales Method
Table Of Contents
Quick Links
Your customer is lying to you about cyber
Your customers know they are at risk, and they’re willing to pay more … But how much more?
Why do customers balk at spending on security upgrades when I offer them?
Let’s Talk About Security Buyer Resistance
The resistance points that are stopping your security sales
Buyer is unsure who to trust with security
Buyer is unsure how much security they need
Buyer has choice paralysis due to fog of more
Buyer has other business priorities to balance
CANT: A framework for preparation-based MSP cyber sales
Preparing your customer for cyber investment
Navigating buyer resistance by preparing for the sale
Set the stage for capturing a security call-to-action – with preparation
MSP Cyber Solution Playbook
Using customer trust to bundle and sell more cyber with the CANT Cyber Sales Method. Preparation based cyber-sales objection handling that works.
Also includes:
- Six (6) illustrated Service Descriptions
- Cyber Solution Reference
Bonus: CANT Cyber Sales Method Poster (8.5" x 11")
Your customers know they are at risk, and they’re willing to pay more … But how much more?
|
“91% of SMBs would consider using or moving to a new IT service provider if they offered the ‘right’ cybersecurity solution… would be willing to pay 30% more for it.” Source: ConnectWise, The State of SMB Cybersecurity |
Surveys and buying data are pretty consistent on this fact, but a successful security upsell has to overcome significant barriers.
Why do customers balk at spending on security upgrades when I offer them?
Let’s Talk About Security Buyer Resistance
Your customer is busy. They’re scared about a cyber fail, but they don’t know who to trust, how much to spend, or what to buy.
Shopping for computers is easy. When one is nice to use, the value is immediately obvious.
It’s no wonder most organizations rely on a “lightning strike” mentality: “There’s nothing I can do, so I’ll hope for the best”.
Buyer is unsure who to trust with security
Customers trust you with their IT, but seem unwilling to accept your advice on security. It’s easy to presume they simply don’t value security, but in its basic form, there’s a trust chasm that’s difficult to cross.
Uninformed buyers have been assaulted with stories about how trusted cornerstones of their worldview are entirely unprepared to defend them from cyberattack.
Software monoliths like Microsoft, US Federal agencies like the Department of Defense or the State Department, and finance sector staples like Equifax and Capital One, have all played the victim on the front page of their social feeds.
When a customer finally decides to accept the advice that they must do something about cyber, they find headlines that are totally counterproductive to the MSP sales narrative, such as:
|
Kaseya Ransomware Attack Triggers Race to Hack Other Managed Services Providers A ransomware attack in July that paralyzed as many as 1,500 organizations … |
Buyer is unsure how much security they need
Customers know they need to do something, but cyber solutions range from interventions that are practically free, to services that cost millions of dollars a year. When a business doesn’t understand what they are buying, it’s impossible to justify an expense that may be too little or too much.
How does your customer test drive a cyber solution when they don’t even understand what it does?
Buyer has choice paralysis due to fog of more
A technologist is familiar with the concept that there are many thousands of subtly unique methods an attacker can use to gain advantage in a cyber attack. How can you sum this up to your customer in a reassuring way?
It’s tempting to cherry pick a couple cyber products and offer them as good ideas. When the customer asks if that will definitely stop an attack, can you tell them that their results are guaranteed? Of course not … you have to explain that to stop the many thousands of ways an attacker can break in, there are hundreds or even thousands of defensive actions that need to be taken, and some of them are more important than others.
Your customer is now lost in a maze of choices. Even if you’re not offering hundreds of choices, the customer knows there are many things you are not offering. How does the customer know you’ve chosen correctly for them?
Buyer has other business priorities to balance
I think everyone in MSP sales is familiar with this problem. On Monday, a customer emergency (or the morning weather report) makes security the business owner’s number one concern. As their MSP, you receive the first call, and promise your customer you have a plan and you’ll deliver them a proposal in a day or three.
By Wednesday (solved or not) your point of contact has moved on, a new business emergency has demanded their attention, and they’re done thinking about cyber until March. The customer says it’s too expensive as an excuse, but the basic reality is they’ve either purchased reassurance elsewhere, or the moment of urgency has passed.

MSP Cyber Solution Playbook
Using customer trust to bundle and sell more cyber with the CANT Cyber Sales Method. Preparation based cyber-sales objection handling that works.
Also includes:
- Six (6) illustrated Service Descriptions
- Cyber Solution Reference
Bonus: CANT Cyber Sales Method Poster (8.5" x 11")
Preparing your customer for cyber investment
BANT, CHAMP and other standard sales frameworks can be used by sales teams to pre-qualify leads before engaging them in sales activities. This allows automation or low-cost labor marketing engines to provide “qualified” leads to individual sales managers who then won’t waste time on customer deals that can’t be quickly closed.
In CANT, we work to win the customer over (remove the reasons a customer “can’t” buy) before they are ready.
- I “can’t” figure out who to Trust with cyber
- I “can’t” decide what cyber Choice is right
- I “can’t” find the Time to focus on cyber
Cyber urgency has a particular cutting edge. Businesses can go from hero to zero in minutes. Your customer will not give you days or weeks to prepare a solution when they need a fire put out yesterday. How do you prepare for this?
Because cyber sales are predominantly driven by immediate urgency, the best way for an MSP to sell cyber is to prepare for the position of “default solution” when a customer’s moment of urgency arrives.
Overcome their resistance or objection points in advance, because you will not have time later.
Navigating buyer resistance by preparing for the sale
It’s an old adage in any type of sales activity. The existing customer sale is the best customer sale.
You’ve already acquired the relationship and customer trust. An upsell is a profitable way to increase revenue because it doesn’t require cold calling, knocking on doors, or advertising.
FortMesa’s whitepaper on the subject is here: Security Service Automation: Double your profit with cross-sell driven margin expansion.
But you’ve got a problem: the things that made you successful in winning a desktop support and general IT services contract do not automatically give you the right to win in security sales.
Set the stage for capturing a security call-to-action – with preparation
Becoming the Default Option through Security Credibility
Your customer has already chosen to rely on you for IT, and they think your offering is great. You didn’t need to give them the advanced cyber capability pitch to get their business because they didn’t think they needed it.
Does that mean they trust you with cyber? How good is your lowest cost offering really protecting them against today’s threats?
Clearly, they have not crossed the threshold where formalized investment in cybersecurity is required if they have not demanded more. In a larger or mature business, this happens once when strategy changes due to growth in size or complexity.
Smaller or less mature organizations tend toward tactical thinking. They are concerned with what they need now, and security needs are not always urgent.
CANT: The “Trust” Pillar |
|
|
Resistance Point |
How to Overcome |
|
Buyer is unsure who to trust with security. |
Establish yourself as a credible security authority. |
How does this work? Tell them in a conversation.
- You have an advanced security offering that reduces cyber risks
- It’s really good for businesses looking for strong security assurance
- It’s very helpful when customers, partners or insurers demand cyber due diligence
- It clearly evidences industry standards and regulatory compliance
- It costs more, but your basic offering is also a good value point if they don’t need more.
- Any time they want to upgrade, it’s very simple to switch
What else? Don’t just tell them, show them.
- Show them their company’s security panel
- Illustrate exactly what security they have now
By the end of this conversation, you have not won the cyber sale, but your customer knows you’re already offering good security value, and an advanced offering is available if they need it.
Make Recommendations to Protect Your Customer and Yourself
CANT: The “Choice” Pillar |
|
|
Resistance Point |
How to Overcome |
|
Buyer is unsure how much security they need. |
Explain how your customer should choose their security tier, by explaining your tiers. |
|
Buyer has choice paralysis due to fog of more. |
Do not provide a menu of technical security options. Your customer already trusts you with IT, they should choose outcomes (you choose tech). |
Hopefully you’ve already taken a bite out of the trust problem, and in doing so you’ve made cyber less scary. It’s time to move onto the choice pillar.
Formalizing Risk Acceptance
Ask all your customers to accept residual risk. The following page contains a minimal cyber risk acceptance form.
To simplify the process, this form is intended to be filled by the MSP in a verbal interview, then signed by the customer. You could interview the customer while showing them their security dashboard, and then send them this paper afterward (conquer trust and choice at the same time).
The intent here is to:
- Conform to cyber best practices by formalizing risk acceptance
- Provide the MSP with information about the risk environment
- Provide the customer with recommendations they can act on when they are ready
While both parties are afforded additional legal or liability protections by completing this process, the intent is not to transfer risk or shield the MSP from liability.
If your customer is scared, you could weaken the verbiage depending on your preferred mode of customer engagement and achieve the same results. The intent here is to draw a line in the sand and force the customer to make a choice.

MSP Cyber Solution Playbook
Using customer trust to bundle and sell more cyber with the CANT Cyber Sales Method. Preparation based cyber-sales objection handling that works.
Also includes:
- Six (6) illustrated Service Descriptions
- Cyber Solution Reference
Bonus: CANT Cyber Sales Method Poster (8.5" x 11")
Educate your customers about your cyber offering
Your customer has probably already made a choice, but it’s important the customer knows how their choice relates to your offerings.
Early security conversations with a customer should be focused on establishing your company as a security brand. The offering details are not important (and counterproductive) if they are not feeling the type of urgency or need that stimulates security investment.
As part of the risk disclosure, you’ve made a recommendation.
Following the sample risk acceptance form is an example offering sheet you might provide a customer who is not ready for advanced cyber now (but might be in the future). This briefly explains the recommendation.
Unless the customer asks for a dedicated briefing on your advanced security tier (or have a cybersecurity urgency), stop here.
Sample “Choice” pillar security acceptance form
|
Reference MSP Cyber Risk Disclosure Form |
|
|
Company Name ________________________________ Availability My company will be significantly impacted by extended periods of “Downtime” No significant business impactSignificant business impact My company will be significantly impacted by “Data Loss” No significant business impact Confidentiality My company will be significantly impacted by improper disclosure or a “Data Breach” No significant business impactSignificant loss of public confidence (reputation impact) |
# MSP Managed User _________________ # MSP Managed Devices ______________ Sensitivity of data The data environment in my business Mostly limited to employee and financial information A failure in my organization’s security can cause significant harm to public welfare No public harm is possibleSignificant public harm is possible
|
Based on the information provided, Reference MSP recommends: Basic Security BundleAdvanced Security Bundle Added Network Monitoring Other special security service(s) _________________________________________________________________ The above disclosures are true and correct to the best of my knowledge. I understand no commercially reasonable security can eliminate 100% of residual cyber risk, and following industry standard cybersecurity standards is the best way to reduce risk. I understand Reference MSP has made risk management recommendations based on standard practices, and failure to adequately invest in cybersecurity will expose me to additional residual risk. I accept all residual cyber risk: Signed: __________________________________ Print Name: __________________________________ Date: _______________________ |
|
A note about “Backup” waivers
Some MSPs ask their customers to sign waivers that they are not responsible for data loss if the customer chooses not to implement an optional backup strategy the MSP thinks is a good idea.
A customer resistant to buying backups will frequently be converted by the clear waiver and signature requirement. After all, if there’s a loss, they can no longer blame you.
If you do this for backups, consider issuing this for cybersecurity at the same time.
Example “Choice” pillar security offering one-page glossy
Reference MSP Cyber Offerings |
|
| Basic Security | |
|
Price Per user per month (but per device is also an option) |
$0 You include good security value for every customer. |
| What it includes |
A set of basic customer practices. This can simply formalize what you already do for all your customers.
|
| When to choose | Customers looking for good protections against cyber threats. |
| Advanced Security | |
|
Price Per user per month (but per device is also an option) |
$30-75/user/month You price cyber as an add-on to standard technology support. |
| What it includes |
A set of advanced customer practices
|
| When to choose |
Customers looking for better protection that eliminates most cyber risks or customers that:
|
| Advanced Add-on | |
|
Price Per user per month (but per device is also an option) |
Additional “Best” Upgrades as needed. Advanced Add-ons require Advanced core.
|
| What it includes | |
| When to choose | |
Affirm their choice (they are the buyer), don’t forget to finish preparation
Remember: You will not succeed unless your customer has a security imperative or urgency.
Affirm your customer’s choice not to invest more in cyber. It’s important to validate their risk decision.
You cannot rush the customer’s investment, but you can frame the conversion point by reminding them what their choice not to invest means:
- Security incidents may not be considered an emergency by the MSP, unless the customer has selected Advanced Security.
- On basic tier, security incidents have the same SLA as other non-security issues
- They can upgrade at any time
- You think your basic security is pretty good, but you can’t support any due diligence effort or provide documentation or certification.
- The centerpiece of your advanced tier is risk management and cyber assurance, and you really can’t provide that to them unless they’re assigning dedicated security resources
- If they upgrade, you can turn this around very quickly. It may take time to get all the protections in place, but an attestation that the customer has committed to a specific security roadmap is powerful and you can issue point-in-time attestations as soon as they sign.
- Help them recognize circumstances they might see in the future that would indicate they need to upgrade
Recognizing the Call To Action (Moment of Security Urgency)
The above resistance points are difficult to overcome quickly. In fact, it is commonly accepted (or decried) in the security industry that organizations simply don’t care until they do (when it’s often too late).
Circular logic may not sound helpful, but it’s a recognition of the fact that an outside force is needed to push a customer into an investment. While there are nearly universal resistance forces working against a security sale, moments of urgency are equally universal.
To successfully capture the moment of urgency, it must be recognized, and the recognition needs to begin with the customer (they need to tell you it’s happening).
Help your customer by explaining likely situations that may mean they need to rethink their cyber risk acceptance.
CANT: The “Timing” PillarMoments of security urgency are moments of security investment |
|||
|
|
Due Diligence |
Security Incident |
Regulatory Pressure |
|
Common Example |
Sales objection over cyber credibility or customer’s vendor requirements |
An impacting security breach that led to lost business or dollars |
Need to be perceived as regulatory compliant |
|
Less Common Example |
Non-customer stakeholder seeks cyber credibility over potential partnership or transaction |
A non-impacting security incident that created a wake-up call |
Actual pressure from a government regulator |
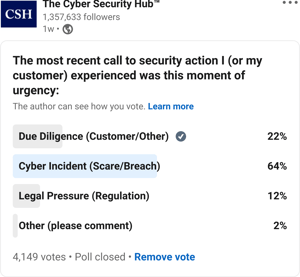
Understand your customer. Ask them what types of cyber pressures they think they may face in the future and when. Give them some examples of situations that are likely. Keep these in your customer notes and ask about them in business reviews.
Your customer will remember frequently discussed security pressures and recognize them when they occur.
When your customer tells you the moment has arrived, remind them that you’ve already game-planned the potential response.
It’s now time to initiate the hard sell.

MSP Cyber Solution Playbook
Using customer trust to bundle and sell more cyber with the CANT Cyber Sales Method. Preparation based cyber-sales objection handling that works.
Also includes:
- Six (6) illustrated Service Descriptions
- Cyber Solution Reference
Bonus: CANT Cyber Sales Method Poster (8.5" x 11")
Responding to the Call
The situation you should not be in
If you have not prepared for responding to the call, here’s the most likely scenario (is this familiar?)
- Your customer calls you with an emergency security situation (see table above)
- You drop whatever you are doing and respond to their issue immediately, but tell them that they are underinvested in cyber. The customer agrees and asks for options, but ultimately they’ve only got eyes for the fire in front of them.
- In a day or three you respond with pricing on a MFA hygiene agent, some EDR wizardry, a vSOC or XDR option, and of course they can start scheduling some vCISO time focused around holes they need to fill so they can prepare for an audit from a cyber shop you’re happy to introduce them to later
- Your customer graciously acknowledges the proposal or ignores it. When you ask for a decision your customer tells you they can’t really afford it after all.
What went wrong?
- Not only is your emergency response unnecessary (if the customer was better secured, there would be no emergency), you’ve got a low probability of actually satisfying the customer. Even if you scramble, nothing you create or fix in a few minutes is going to make up for a breach that has already happened, the lack of a documented security architecture, or a misalignment with industry regulations.
- Your customer’s moment of urgency was either (a) not resolved with an ideal outcome, (b) entirely preventable, or (c) not successfully converted into a service upgrade.
The mindset of a prepared customer
If you’ve done your job before your customer reached their moment of urgency, these are already facts they know:
CANT in actionIngredients of successful preparation based security sales |
|
|
Before the moment of urgency you have: |
What this means now (customer viewpoint fact): |
|
Established yourself as a security vendor by showing the customer their current security |
You are the default security vendor. |
|
Mentioned you have an advanced security offering |
You get the first call when the customer decides to shop |
|
Forced the customer to disclose risk and choose |
The customer knows they are in control of the security dial |
|
Affirmed the customer’s choice of “good” security |
Your offer feels strategic rather than opportunistic. You are both cost effective and credible. |
|
Introduced your advanced security package, but held back on details |
Your customer knows you already have the plan cooked (not much thought required). |
|
Described the moment of urgency to them |
Your prediction was prescient, thus your insights and previous recommendations have value. |
Capturing the Moment
The moment of urgency arrives. You’ve already prepared the customer, right?
If you’ve already prepared the customer, they probably realize their first words to you should be “I’m ready for an upgrade, so how fast can you do it?”
It’s possible your prep script still needs a little bit of work, or they’ve disassociated your preparation from their current situation. Remind them about your advanced offering and tell them you’re happy to continue trying to help them, but their basic tier does limit what you can and can’t do.
This is when you offer the advanced security briefing. Be clear, they need the advanced tier to obtain advanced security value. You can’t break the bundle because you only have normalized service tiers.
This should happen during the moment of urgency. If you wait until the customer’s problem has been resolved, security will suddenly seem too expensive (they didn’t need it, right?)
Before we discuss the briefing, let’s talk about how you can accomplish the simple service offerings above.
|
CANT Visual Summary Level-up your Cyber Sales with Pillars of CANT |
|
|
|
Trust Choice Timing |
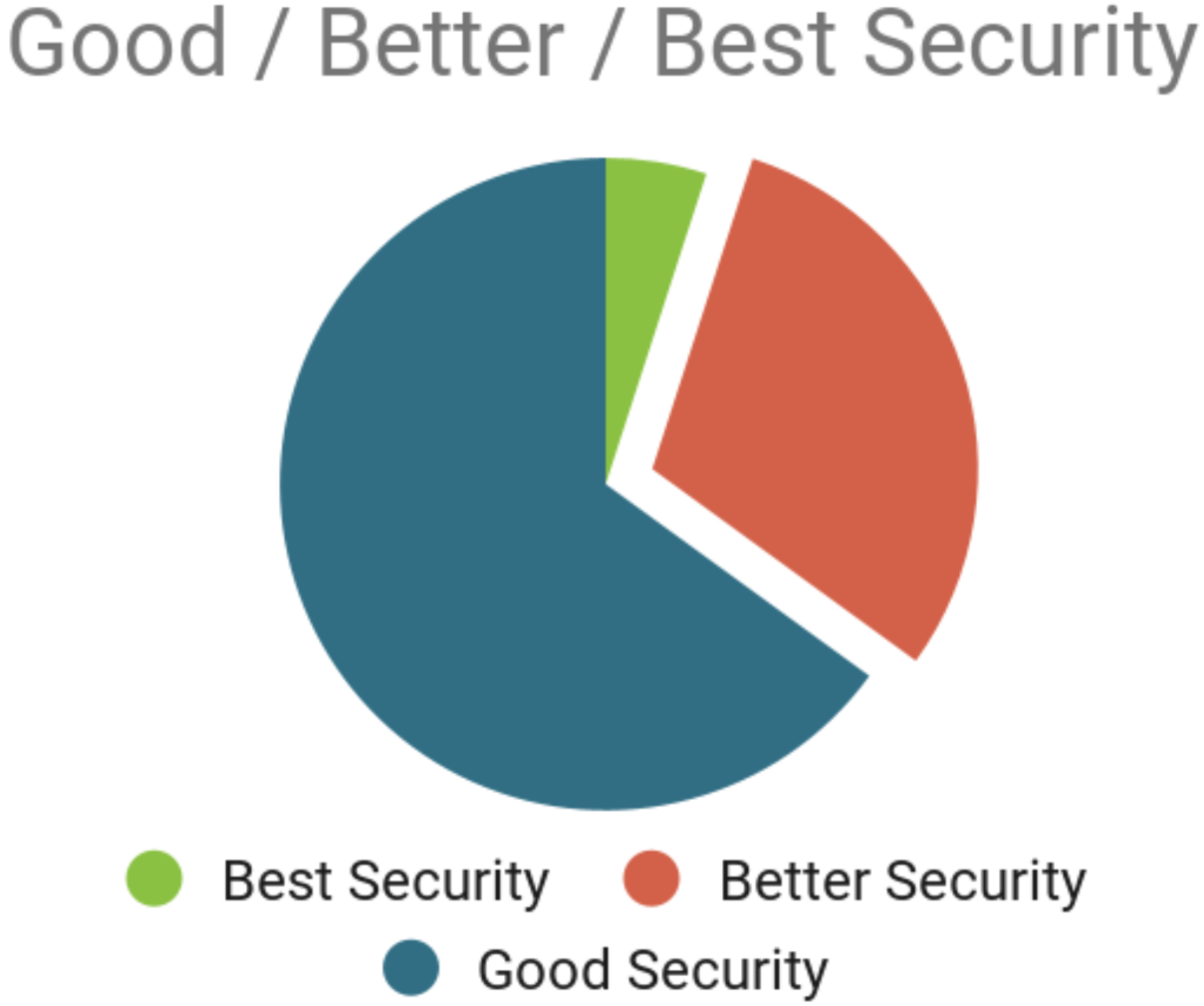
What should I expect from my customers over time?Data show most customers are willing to pay more, but moments of urgency are not operated by clockwork gears. You know your strategy is succeeding when a substantial number of customers opt-in to “better” security.
|
|

MSP Cyber Solution Playbook
Using customer trust to bundle and sell more cyber with the CANT Cyber Sales Method. Preparation based cyber-sales objection handling that works.
Also includes:
- Six (6) illustrated Service Descriptions
- Cyber Solution Reference
Bonus: CANT Cyber Sales Method Poster (8.5" x 11")
Next Steps
Build the Bundle
Each of your security bundle tiers should be based on the standard security baseline established by an independent security authority.
There are dozens of security standards one might choose that would be recognizable in a specific customer segment. Some of these standards have levels of implementation based on the circumstance of the organization or system being protected.
Finding an independent standard to point to as the focus of your company’s security strategy is the basis of best practice cyber risk management.
For a complete "Build The Bundle" guide continue reading the full playbook.
Download the EBOOK for the complete guide.

MSP Cyber Solution Playbook
Using customer trust to bundle and sell more cyber with the CANT Cyber Sales Method. Preparation based cyber-sales objection handling that works.
Also includes:
- Six (6) illustrated Service Descriptions
- Cyber Solution Reference
Bonus: CANT Cyber Sales Method Poster (8.5" x 11")
Explore cyber best practices
Read more about the tools and concepts needed to deliver cybersecurity that will protect your company and your customers
.png?width=250&name=Cyber%20Sales%20with%20Pillars%20of%20CANT%20(2).png)