Building Effective Security Teams
Cyber defense is a team sport with varied roles that need to be filled in a balanced way. Let’s take a high level look at what it takes to successfully orchestrate a security team.
Prerequisites for Security Success
Executive Mandate
Accountability for any action or inaction in an organization always rolls up to the CEO and ultimately the board of directors. For this reason a successful security program needs high level executive authorization and reporting.
The best way to formalize this executive mandate is with a security charter. This simple document authorizes the widely-ranging activities of a security program and clarifies its importance to all stakeholders.
Stakeholder Buy-in
Just like any sports team you can think of, weaknesses in your security team can and will be exploited by the opposition. To use another analogy consider that a garden fence with a single small hole will admit rabbits.
It’s important that every individual with a role to play in a security program understands how they fit into the larger team, why their participation is important to security, and the value security provides.
We’ll talk more about the specific stakeholders who actively participate in a security team below.
Risk Management
You can’t efficiently or effectively defend anything without a plan. Risk Management is the methodology used to devise and operate your security plan.
Security Culture
The executive mandate, stakeholder buy-in, and a risk management philosophy are the ingredients required to create a security culture.
The Role of the CISO
Security strategists differ on what qualities a CISO should have and where their job begins and ends. In its most basic form the role of the CISO is simply a designated delegate who is responsible for the overseeing of an organization’s security program.
By assigning the CISO role the CEO has demonstrated due care, but due diligence is also required. It’s the CISO’s job to make sure the security program operates as intended.
This person’s job is to make sure the strategy is sound, the resources are effective, and the technologists, security/risk workers, and other stakeholders are all working together.
In a large mature security organization a CISO is ideally a bridgemaker with both a strong grasp of business skills and the requisite technical engineering background to understand cyber risks and technology at a detailed level.
In a smaller organization, or in early stage security program management it is simply enough that this person has the acumen to evaluate whether all the other players are being effective and that they care enough to drive the operation of the security program. The use of external guidance is critical here.
Security Stakeholders
Many attempts have been made to formalize the roles inherent to operating a security program and managing information assets. The following should be considered a succinct summary of best practice.
- Business Owners – CEOs or Business Unit Executives
- A business owner has the primary due care burden (and this can not be delegated). It’s the business owners job to make sure cyber risk is not a threat to the operation of their business.
- Some organizations can be effectively broken into Organizational Units (eg, a conglomerate), but if information assets are shared across the organization it is best to consider a single business owner.
- Asset Owners (or System Owners)
- These are individuals responsible for the procurement and requirements of an information system. It can sometimes be difficult to identify the best Asset Owner for a particular asset, but it’s important this is done with care.
- Examples
- The Director of Sales is always the Asset Owner for Salesforce even if he doesn’t know how to use a computer.
- A clerical worker with a dedicated computer is the Asset Owner of their PC even if they don’t have rights to install software.
- Despite the fact the IT department helped in procurement of the ERP system, the Asset Owner is probably the COO.
- Asset Custodians (or System Custodians)
- These individuals are responsible for the deployment, operation and maintenance of an information asset.
- Examples
- An individual who “Brings Their Own” mobile phone is likely the Asset Custodian.
- The same mobile phone under Mobile Device Management is probably assigned to an IT Custodian.
- Data (Asset) Stewards
- Mature security programs with an emphasis on the integrity of data will assign Data Stewards to make sure the data is accurate. They do this on behalf of an Data Asset Owner, and may work with the Data Asset Custodian (who is probably responsible for backups).
- Information Security Officers (often just CISO)
- The Information Security Officer has the highest operational authority to manage the security of information in a business.
- Security Engineers & Analysts
- We often think of these people as the “security team” despite the fact the team actually includes all the above stakeholders. These technologists are responsible for Red Team and Blue Team activities. They have in times past also been nicknamed White Hats.
- End Users
- It’s easy to forget there are many individuals and interests both inside and outside the organization which are affected by security successes and failures. Many of those affected have no direct role in the security of a cyber or information resource they rely or depend on. All members of the security team need to work together in the interest of end users.
For more detail consider the guidelines present in standardized risk frameworks like NIST CSF, NIST SP800-53, ISO 27000, and ISACA COBIT.
Blue Team (Defenders) vs Red Team (Attackers)

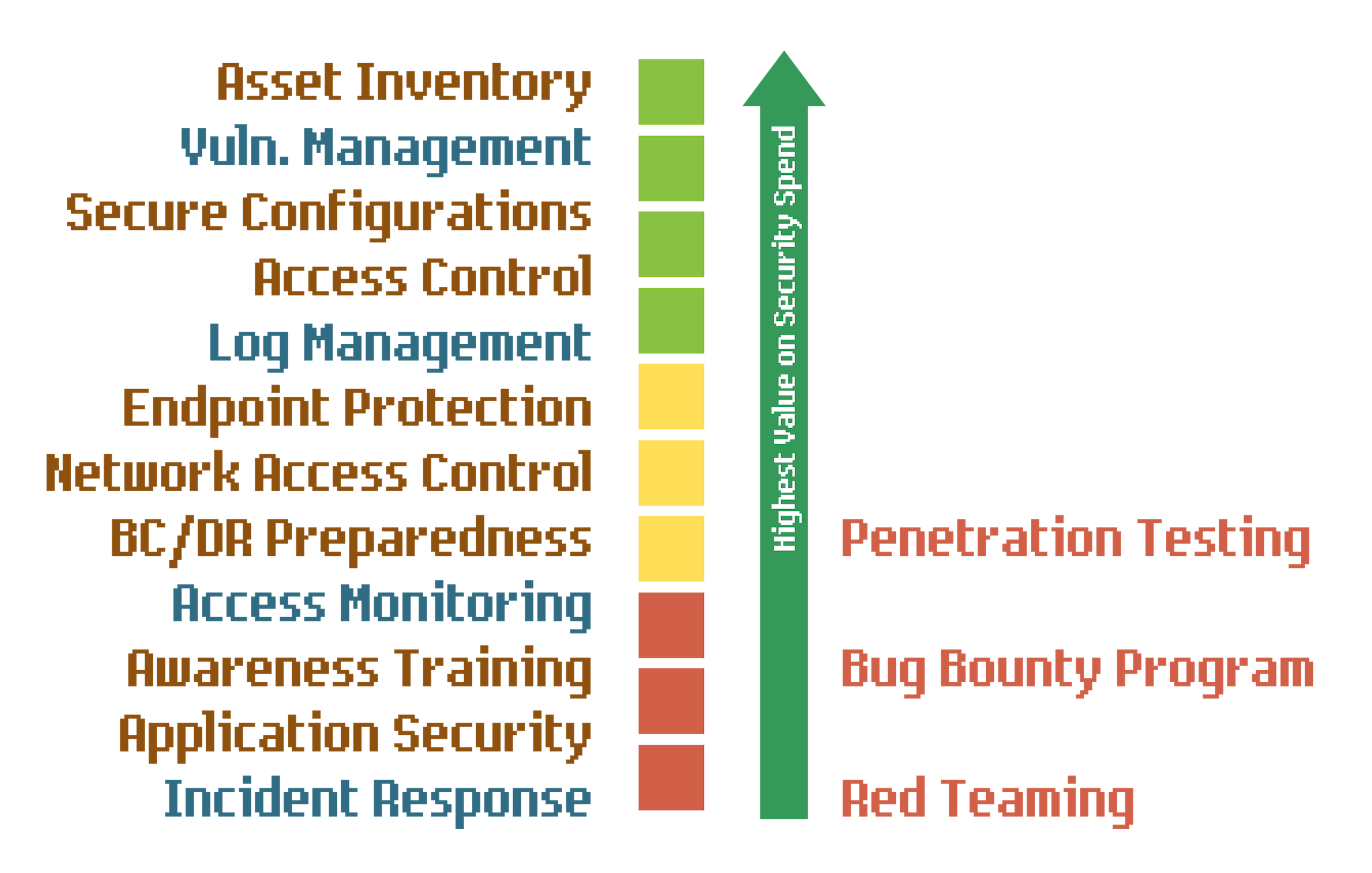
Defensive Blue Teams
Though blue team activities tend not to have much public awareness, this team is responsible either directly or indirectly for most security spending.
Though deployment and operation of security controls depends on help from all over the organization (with big assists by technologists) the blue team determines what security strategies and controls to deploy to effectively combat perceived threats. Anticipated or experienced attacks inform this work.
In addition to the strategic work often delivered in the form of a policy implemented elsewhere, the blue team takes an active tactical role with controls they are most well suited to operate directly. Examples here may include Vulnerability Management, Anomaly Detection and Incident Response.
The Blue Team also correlates security measurements or benchmarks to form a comprehensive picture of security posturing. This “what’s right” and “what’s wrong” work can provide management with feedback on effective resourcing, as well as steer strategic security deployments.
Offensive Red Teams
The real world presents plenty of feedback to sketch the outlines of a security program, but to provide assurance that your security program can effectively combat obscure or focused threats a Red Team can operate a highly sophisticated and tailored campaign to achieve specific goals against a hardened target.
After your organization has completed a comprehensive deployment of security and thinks cyber risks are managed the Red Team validates this thesis.
These individuals might work permanently in a dedicated silo within the company or be contracted from the outside. More and more frequently these are also freelancers working within the bounds of an authorized program.
The Purple Team
“Red Team” and “Blue Team” activities don’t need to be done by separate individuals. While one can hardly attack and defend at the same time, teams can be integrated and members can work closely together or even switch places. In organizations where this is common practice the label “Purple Team” has become an effective moniker.
Indirect Risk Workers
Some of you a little more familiar with GRC may wonder how auditors and other risk workers fit into the security team. There are many types of risk workers who play secondary or indirect roles in security. Though not a part of regular security operations they can influence the overall security culture.
To extend the team sport analogy these might be considered referees or commentators.
There are many great resources on risk management and those subjects deserve distinct attention. A few roles worth noting here are below.
Insurance Underwriters
One way to make yourself safe from cyber risks is to transfer the risk to another entity. With risk transfers in the form of an insurance product, the insurance underwriter sets a price on the risk transfer. The policy premium price (and how it’s set) as well as inclusions/exclusions and coverage/limits provides an incentive to increase or decrease security resourcing.
Risk Auditors
For any number of reasons it is often important to document and correlate risk across an organization using either quantitative or qualitative means. Risk auditors perform data collection and analysis using any number of methods to report on risk and risk management efforts. Stakeholders can self audit, relegate the effort to a distinct team or even contract with independent outsiders for maximum objectivity.
Regulators
In some cases externalities or failures of market economics to protect common good require the need for statute to set rules of the road. Effective cyber risk management typically makes regulatory compliance simple, but regulators set the redlines and the security team needs to maintain awareness and communicate regulatory needs to all stakeholders.
Last updated 2019-02-15.


