Resources
What your company needs to deliver cybersecurity
ALL-IN-ONE-GUIDE
Master Cybersecurity Standards
Explore key cybersecurity standards, frameworks, and regulations to boost data protection and ensure compliance.
STANDARDS & FRAMEWORKS
LEARN MORE
NIST 800-171 Updates: What Contractors Need to Know
Stay compliant with NIST 800-171 Rev. 3 to protect CUI and strengthen your cybersecurity for government contracts.
CYBERSECURITY STANDARDS
LEARN MORE
Compliance Changes in 2025: What You Need to Know
Stay updated on 2025 cybersecurity compliance changes, frameworks, and strategies for service providers.
Resources Library
Interview-based research from ChannelCon 2024
Case Studies
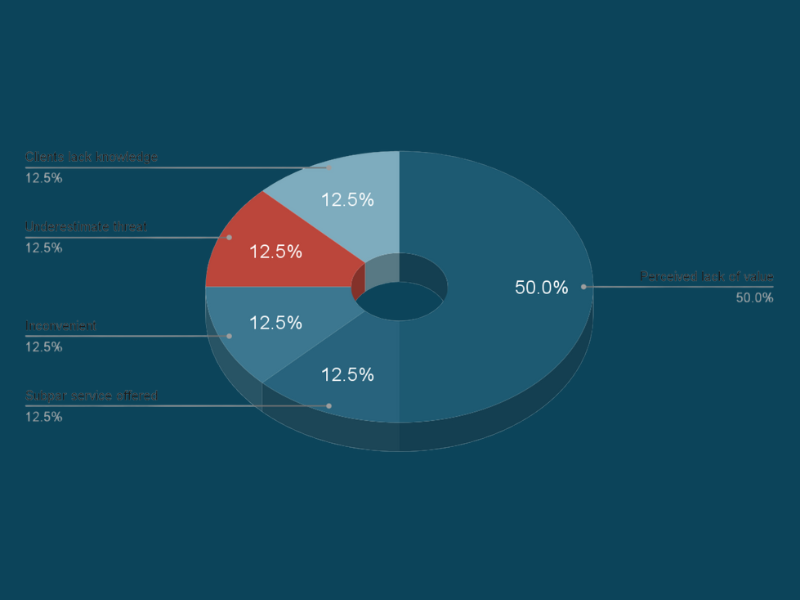
This report, based on CompTIA ChannelCon 2024 interviews, reveals why SMBs resist advanced cybersecurity.
View DetailsInterview-based research from ChannelCon 2024
Case Studies

This report, based on CompTIA ChannelCon 2024 interviews, reveals why SMBs resist advanced cybersecurity.
View DetailsCybersecurity Standards
All-In-One Guide
-1.png)
.png)

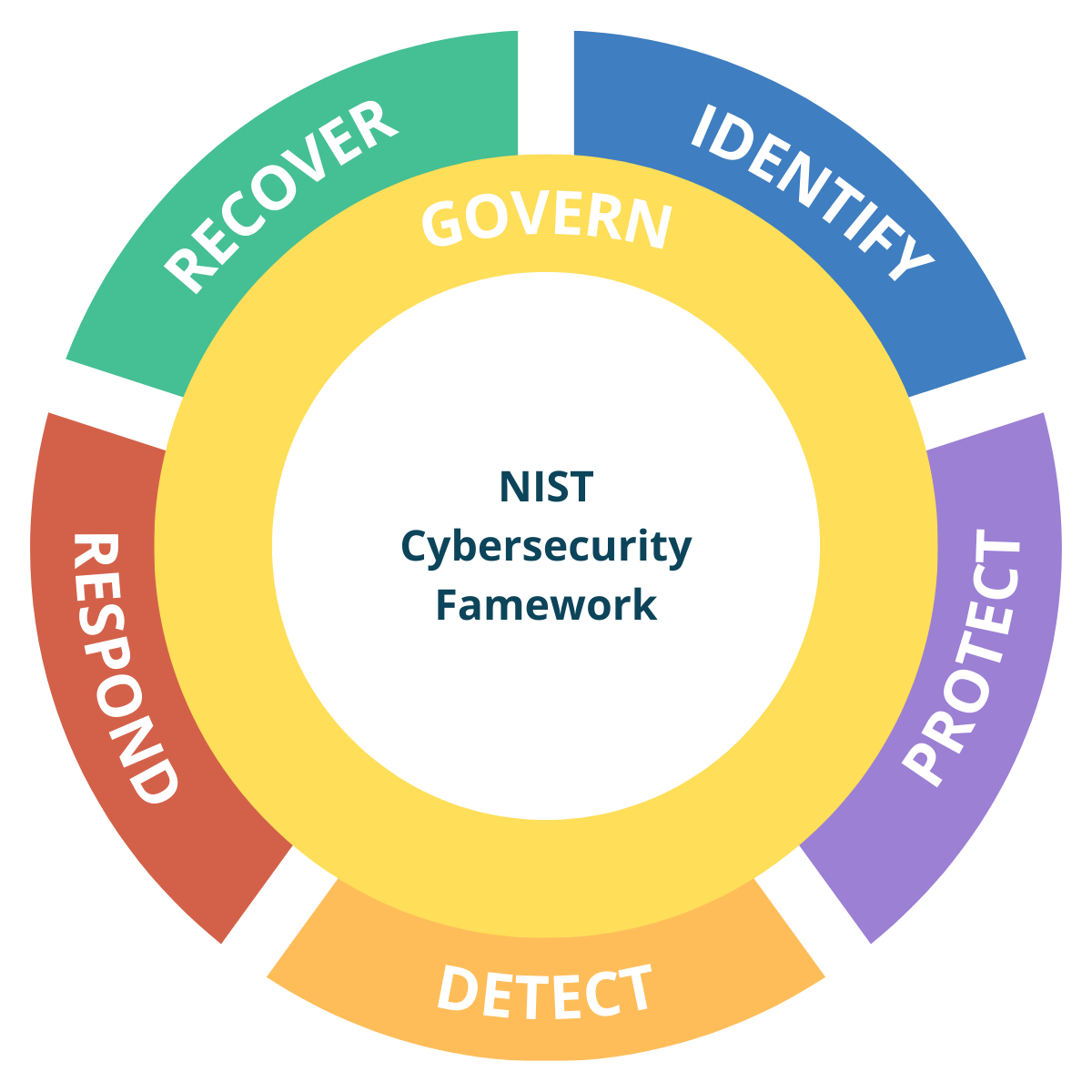
NIST CSF 2.0 Guide for Service Providers
All-In-One Guide
CIS Controls v8 Guide for Service Providers
All-In-One Guide
.png)
-1.png)
.png)
What is Governance?
Article


What's new in CIS Controls V8.1?
Article


SOC 2 Compliance Essentials
Article
.png)
Vulnerability Management 101
All-In-One Guide

-1.png)
Teambuilding 101
Article

Red vs Blue
Article

MoveIT Vuln 90 Days Later
Livestream





Elevating Service Providers Security Standards
Case Studies

FortMesa Empowers IT Providers With Educational Workshops for Cybersecurity Service Excellence
Pressroom

Unique Risk Profiling System Open Door to Cyber Insurance for Previously Uninsured Businesses
Pressroom

.png)

.png)

.png)
Unique Risk Profiling System Opens Doors to Cyber Insurance for Previously Uninsured Businesses
Case Studies

.png)
Cyber Pricing & Packaging
Workshops

Prepare for the Win
Workshops

Talking about Cyber
Workshops

Vulnerability Management
Workshops

Continuous & Periodic Risk Assessments
Workshops

Map the Stack, be the vCISO
Workshops


MSP Cyber Solution Playbook
E-Book

Conquering Cyber Price Objections
Livestream

Cyber Education Guide
All-In-One Guide
A Guide to ISC2 Certifications
Article
Cybersecurity Certifications for Individuals
All-In-One Guide
Understanding Rainbow Tables
Article
The Fundamentals of Encryption
Article

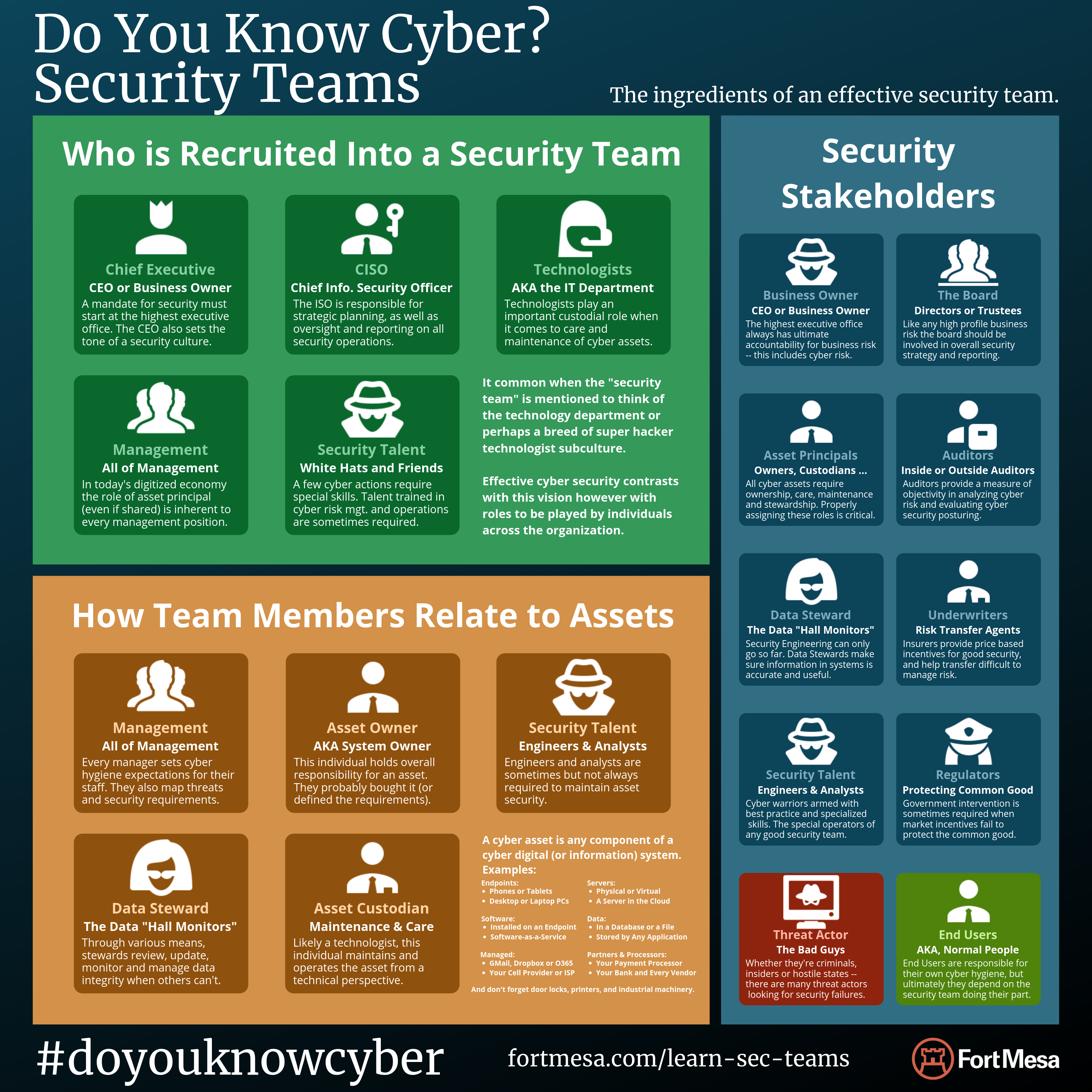
Learn About Security Teams
Article

Get Weekly Updates
Join our newsletter for the latest cybersecurity insights, tips, and updates. Sign up now.