Resources
What your company needs to deliver cybersecurity
ALL-IN-ONE-GUIDE
Master Cybersecurity Standards
Explore key cybersecurity standards, frameworks, and regulations to boost data protection and ensure compliance.
STANDARDS & FRAMEWORKS
LEARN MORE
NIST 800-171 Updates: What Contractors Need to Know
Stay compliant with NIST 800-171 Rev. 3 to protect CUI and strengthen your cybersecurity for government contracts.
CYBERSECURITY STANDARDS
LEARN MORE
Compliance Changes in 2025: What You Need to Know
Stay updated on 2025 cybersecurity compliance changes, frameworks, and strategies for service providers.
Resources Library
Interview-based research from ChannelCon 2024
Case Studies
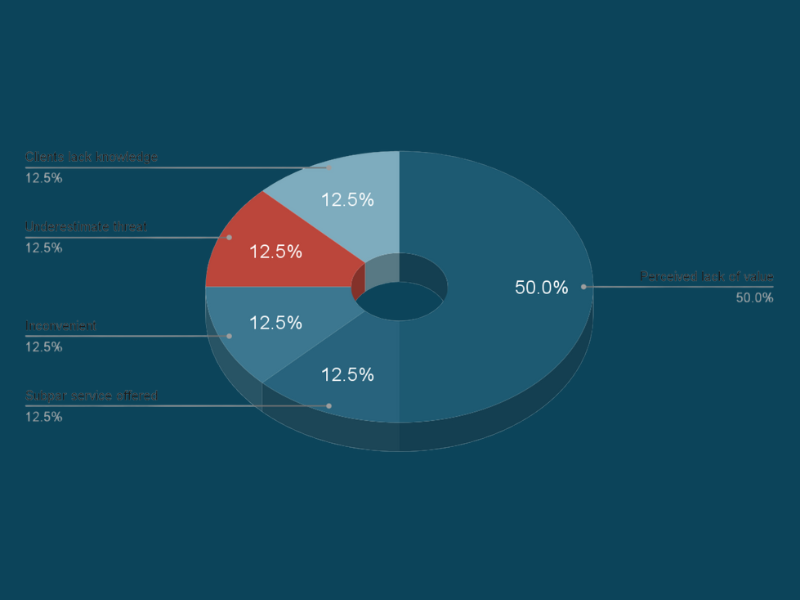
This report, based on CompTIA ChannelCon 2024 interviews, reveals why SMBs resist advanced cybersecurity.
View DetailsInterview-based research from ChannelCon 2024
Case Studies

This report, based on CompTIA ChannelCon 2024 interviews, reveals why SMBs resist advanced cybersecurity.
View DetailsCybersecurity Standards
All-In-One Guide
-1.png)
.png)

NIST CSF 2.0 Guide for Service Providers
All-In-One Guide
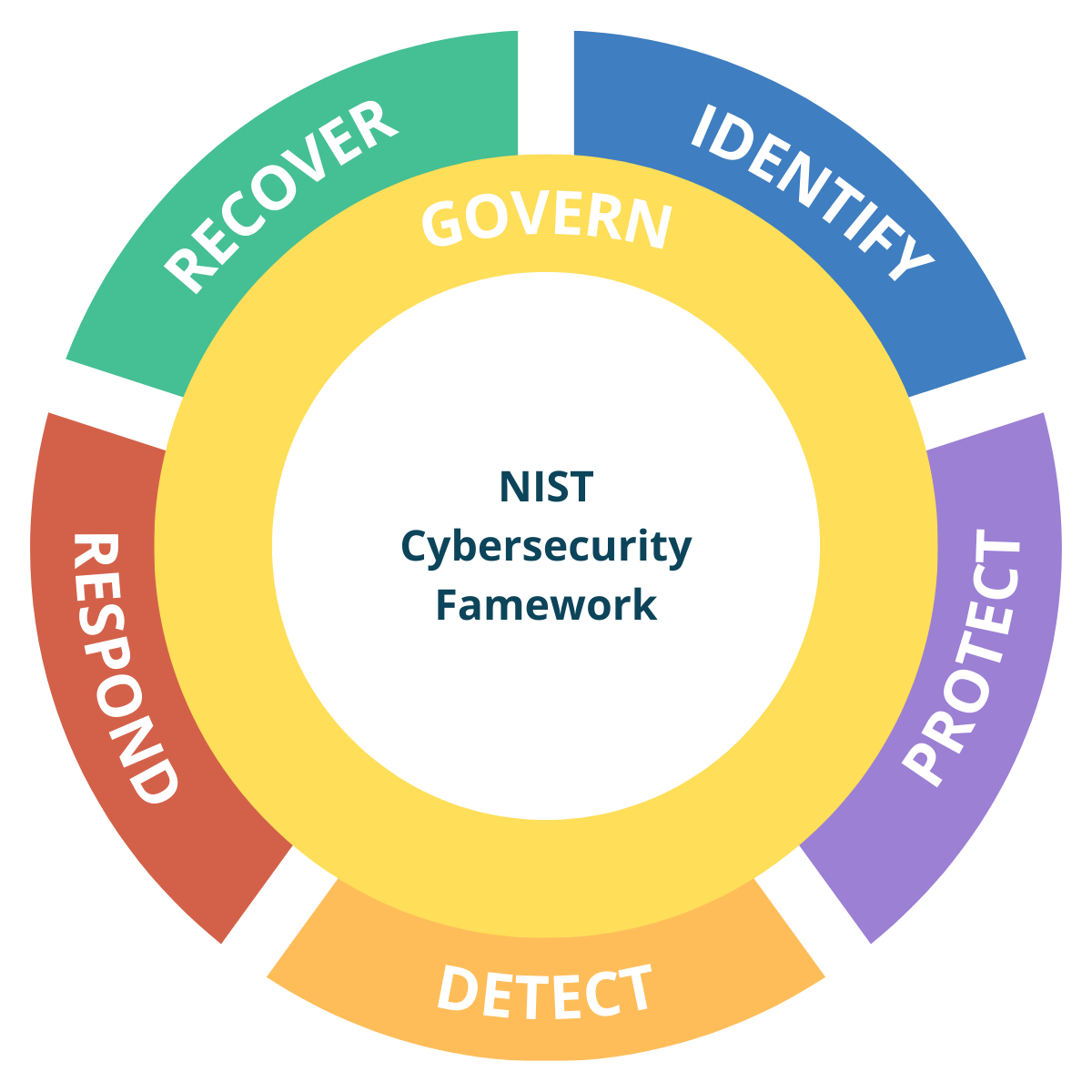
CIS Controls v8 Guide for Service Providers
All-In-One Guide
.png)
-1.png)
.png)
What is Governance?
Article


What's new in CIS Controls V8.1?
Article


SOC 2 Compliance Essentials
Article
.png)
Vulnerability Management 101
All-In-One Guide

-1.png)
Teambuilding 101
Article
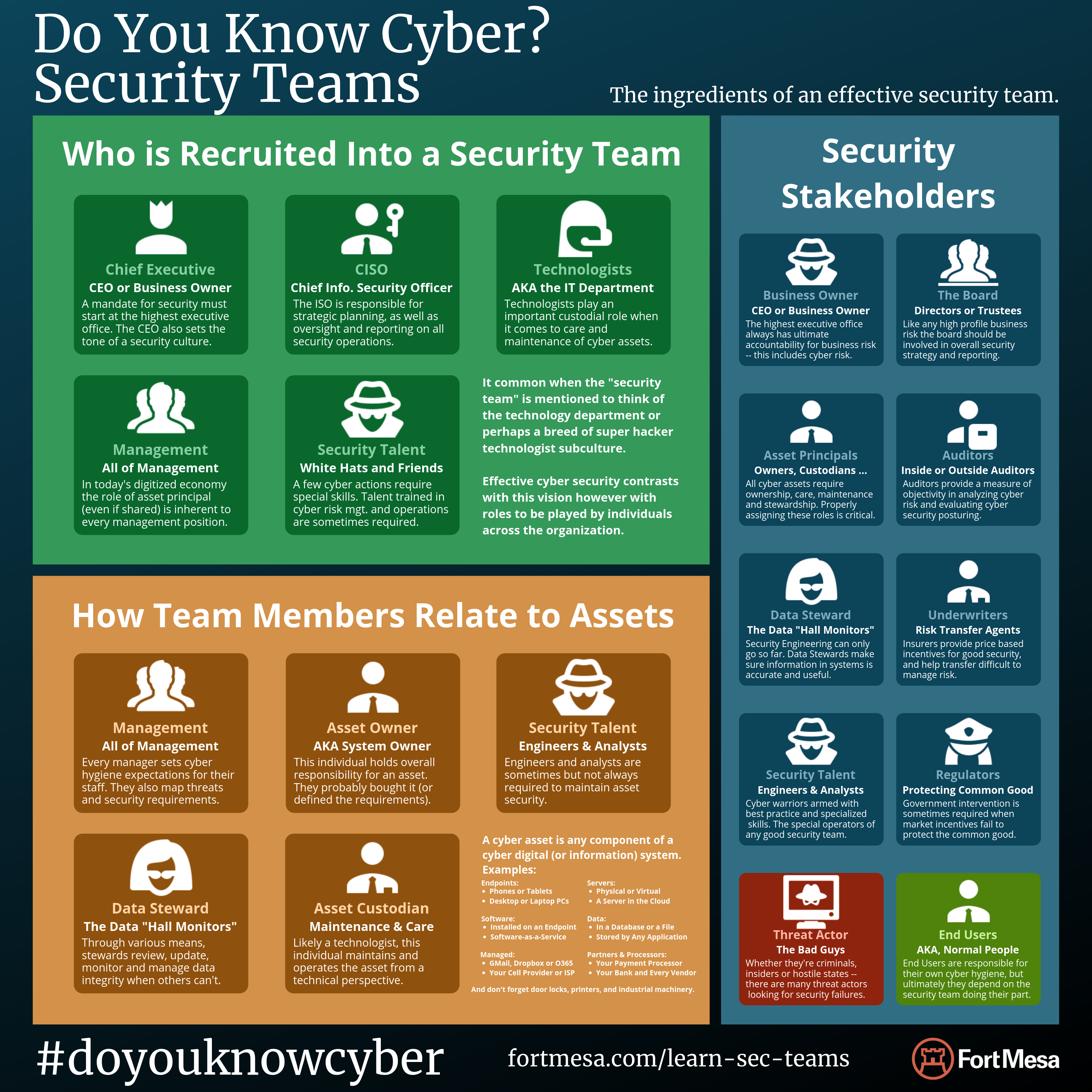

Red vs Blue
Article

MoveIT Vuln 90 Days Later
Livestream


Get Weekly Updates
Join our newsletter for the latest cybersecurity insights, tips, and updates. Sign up now.